

Tidelift


RedMonk


BlackIce


Anchore


HeroDevs


Boeing
In late March, we all dealt with yet another attack on a popular open source project; this time, in the Linux-level package used for file compression called xz utils. What was most sinister about this attack, though, was how deeply it impacted trust within the open source community. The attacker spent years engineering multiple sock puppet accounts to gain the trust of the volunteer xz utils maintainer. In this panel moderated by Tidelift VP of product Lauren Hanford, we’ll talk to Josh Bressers of Anchore; Shaun Martin of BlackIce; Jordan Harband, prolific Javascript maintainer; Rachel Stephens from RedMonk; and Terrence Fischer from Boeing to get a diverse mix of perspectives on how this changes the landscape of open source software supply chain security.
In late March, we all dealt with yet another attack on a popular open source project; this time, in the Linux-level package used for file compression called xz utils. What was most sinister about...
10 questions you should answer before using an open source project
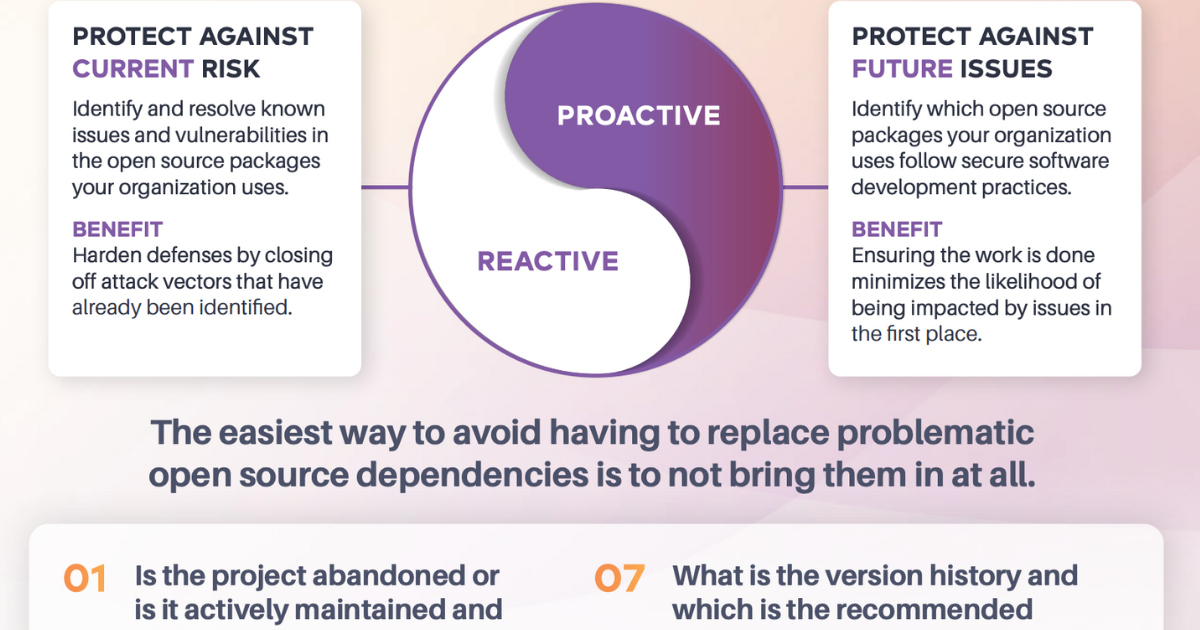
When it comes to open source software security, many organizations rely heavily on software scanning (often called software composition analysis or SCA) as the primary means of defense.

The value of a proactive approach to open source application security
Learn how one large organization saved over $1.6M in manual package evaluation time and eliminated over 3,000 points of risk in applications running in production.
.png)
The guide to reducing security risk from bad open source packages
In this guide, we'll discuss how your organization can reduce risk by avoiding “bad” open source packages.