

Tidelift


Cybersecurity and Infrastructure Security Agency


Cybersecurity and Infrastructure Security Agency
In this session two of CISA’s leading security experts will share more about the industry-wide effort they are leading to make security a core business requirement in products versus an aftermarket technical feature. They’ll share historical analogies of where this design-first approach has had real impact in other industries, and they’ll cover how they are working directly with industry leaders and the open source community to proactively improve practices in ways that will lead to the security outcomes we need.
In this session two of CISA’s leading security experts will share more about the industry-wide effort they are leading to make security a core business requirement in products versus an aftermarket...
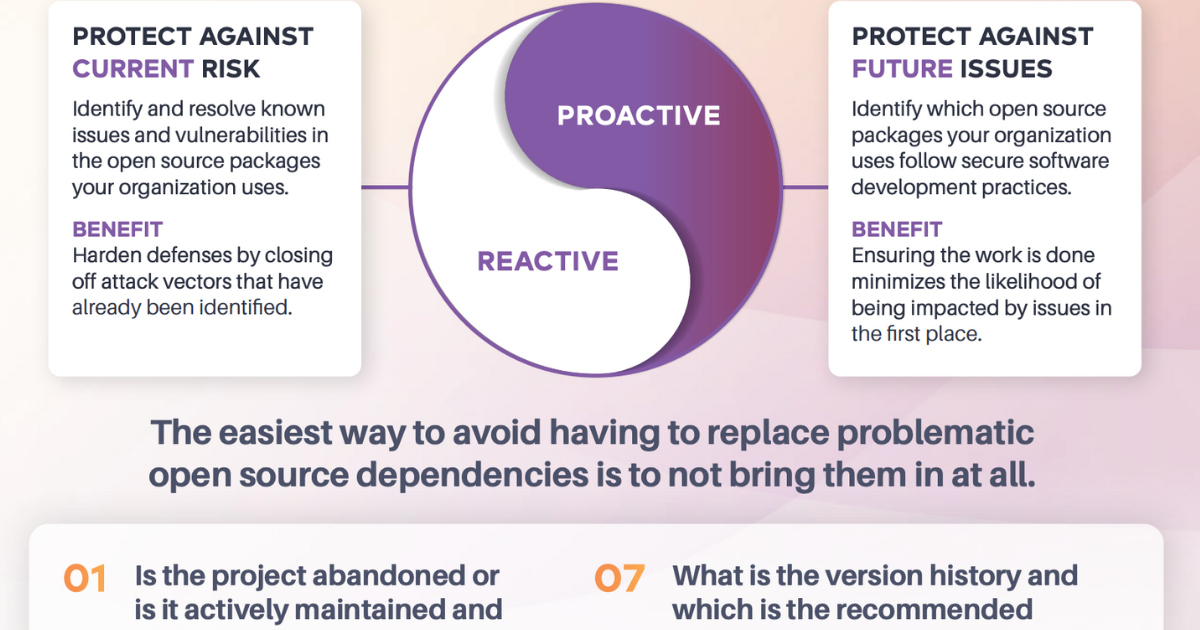
10 questions you should answer before using an open source project
When it comes to open source software security, many organizations rely heavily on software scanning (often called software composition analysis or SCA) as the primary means of defense.

The value of a proactive approach to open source application security
Learn how one large organization saved over $1.6M in manual package evaluation time and eliminated over 3,000 points of risk in applications running in production.
.png)
The guide to reducing security risk from bad open source packages
In this guide, we'll discuss how your organization can reduce risk by avoiding “bad” open source packages.