

Tidelift

When this Canadian telecommunications’ corporate security team came up with directives and policies, they realized that many of these security directives were around open source—and there was no shared foundation in IT on how to follow them. There was no support, tooling, guidance around licensing. This was back in 2019, long before Log4Shell shook the world. This telecommunications company knew that they wanted to leverage the strategic advantages of open source to compete in the telecom market, so they decided to build a process around open source internally, and the OSPO was created. In this fireside chat, Tidelift VP of product Lauren Hanford sits down with Aisha Gautreau, who leads the OPSO at this large Canadian telecommunications company, to hear about the journey of this nascent OSPO and what advantages they have leveraged so far.
When this Canadian telecommunications’ corporate security team came up with directives and policies, they realized that many of these security directives were around open source—and there was no...
10 questions you should answer before using an open source project
When it comes to open source software security, many organizations rely heavily on software scanning (often called software composition analysis or SCA) as the primary means of defense.

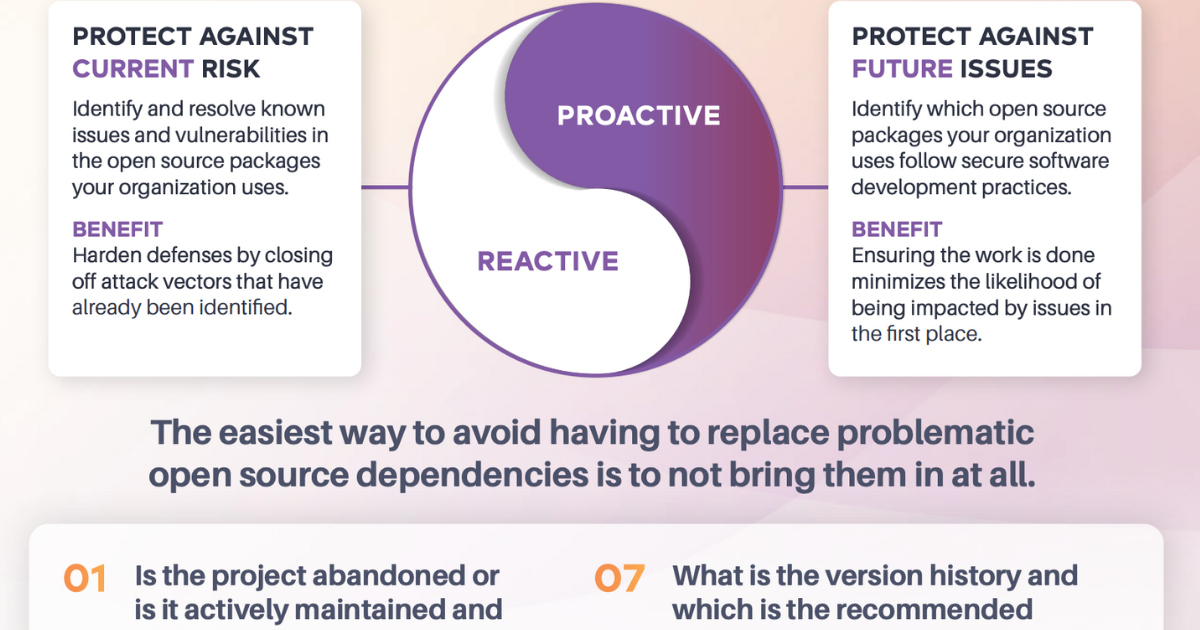
The value of a proactive approach to open source application security
Learn how one large organization saved over $1.6M in manual package evaluation time and eliminated over 3,000 points of risk in applications running in production.
.png)
The guide to reducing security risk from bad open source packages
In this guide, we'll discuss how your organization can reduce risk by avoiding “bad” open source packages.