

Latio Tech / PagerDuty
In this session I'll give an overview of what the problem is with submitting CVEs to GitHub issues—why it's frustrating for compliance teams and maintainers both. I'll cover the nature of vulnerability scanners and compliance requirements that make security teams submit numerous unvalidated vulnerabilities upstream. I'll also talk about why these reports drive maintainers crazy, and the current standards are unrealistic. I'll then highlight how the solution to this problem comes from both sides: clearer maintainer security policies and better understanding of what compliance requirements actually are. I'll talk about why Argo's security policy is a great starting place, and that vulnerability scanners need to focus on upstream direct dependencies instead of the endless transitive dependency pain.
In this session I'll give an overview of what the problem is with submitting CVEs to GitHub issues—why it's frustrating for compliance teams and maintainers both. I'll cover the nature of...
10 questions you should answer before using an open source project
When it comes to open source software security, many organizations rely heavily on software scanning (often called software composition analysis or SCA) as the primary means of defense.

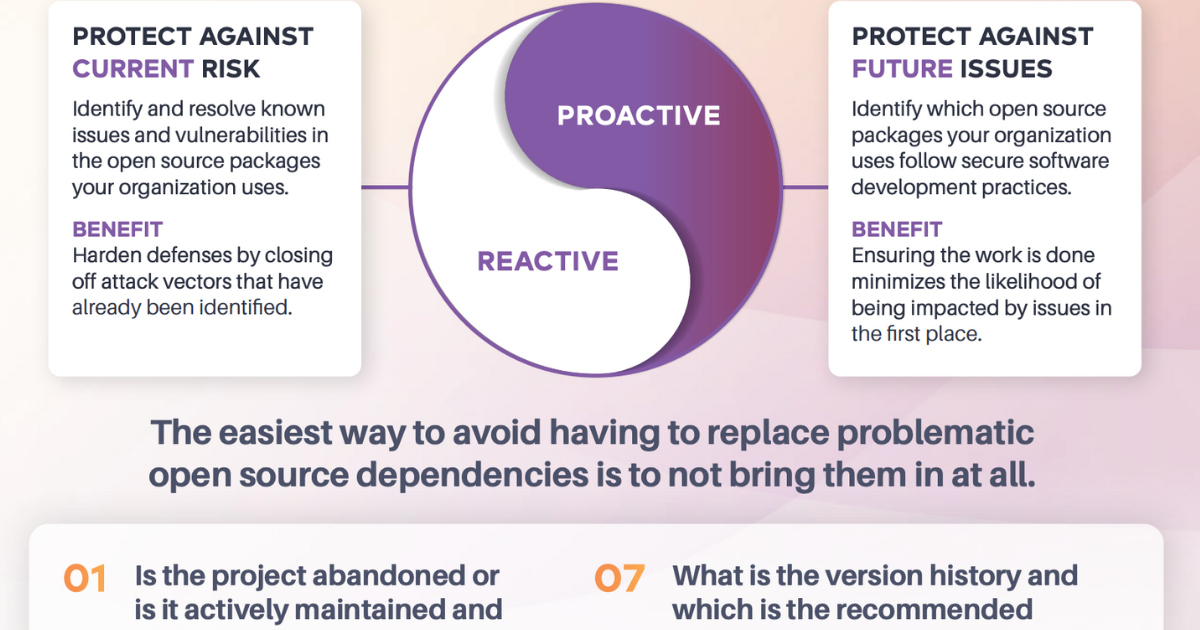
The value of a proactive approach to open source application security
Learn how one large organization saved over $1.6M in manual package evaluation time and eliminated over 3,000 points of risk in applications running in production.
.png)
The guide to reducing security risk from bad open source packages
In this guide, we'll discuss how your organization can reduce risk by avoiding “bad” open source packages.